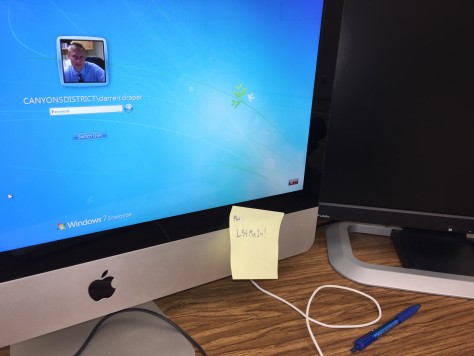
Not long ago, a common scene in many classrooms included a teacher’s computer with an important password – for entry into the computer, teacher gradebook, or even bank account – stickied neatly to its monitor.
There are several reasons for this change. First, online fraud continues to skyrocket. Last year, for example, annual fraud costs to retailers reached $32 billion, with mobile commerce fraud growing at an alarming rate. Second, federal and local government administrators have heightened their sensitivity toward data security, in light of recent high-profile security breaches impacting millions of Americans. These and similar massive data breaches have become commonplace. Third, school patrons and their politically-minded friends continue to grow increasingly concerned about the security and privacy of their data, as evidenced by staggering increases in data protection-related legislation across North America and throughout the world.
Simply put, data security is no longer a casual matter.
So, what are teachers to do? The academic, behavior, attendance, demographic, health, fee, and other data related to students must remain secure; and the demands of the profession require an unencumbered workflow. Therefore, when considering tightened security through shifts in habit and procedure, the impact on convenience should also be reviewed. Are proposed changes, even in the name of security, really worth the hassle?
All told, the safest way to protect student and personal data is likely (although not assuredly) to refrain from using computers, entirely. In one of the most memorable sessions at the 2015 ISTE Conference, Audrey Watters participated on a power-house panel whose intent was to convince the audience that it just might be time to give up on computers in schools. Audrey’s words were chilling, to say the least, and caused many of the ed-technophiles in attendance that day to question the career decisions they’d made up to that point:
Computers and mainframes and networks are a point of control. Computers are a tool of surveillance. Databases and data are how we are disciplined and punished. Quite to the contrary of Seymour [Papert’s] hopes that computers will liberate learners, this will be how all of us will increasingly be monitored and managed…
We live in what law professor Frank Pasquale calls “the black box society.” We are tracked by technology; we are tracked by companies; we are tracked by our employers; we are tracked by the government, and “we have no clear idea of just how far much of this information can travel, how it is used, or its consequences.”
To be clear, it’s typically through the “tracking” that Audrey references that those who would do harm are able inflict the innocent, using data the innocent have failed to protect. Therefore, as teachers – models for a better society – we’re simply not immune to the effects and actions of those with malicious intent. Nevertheless, because our students and their parents live in a hyper-connected digital society, and have come to expect the convenience that technology affords, relinquishing computers is not an option for schools. Instead, we must learn to be savvy by staying one step ahead of the bad guys; just like we’re able to do with our students, each and every day.
We must learn to protect ourselves. We must learn responsible use.
To that end, the first and most important step toward responsible technology use is to understand the basics of data security – required curriculum for all teachers. As teachers, if we’re to model responsible behavior in our stewardship of the data with which we’ve been entrusted, then the following next practices constitute security conventions that must become ingrained within connected classrooms and contemporary school cultures everywhere.
1. Install software updates on a frequent and regular basis. Most major software companies work diligently to keep your data safe and secure by releasing updates to the code they’ve produced. These software patches address known vulnerabilities, but can only work when installed by you or your IT support team.
2. Routinely implement both strong and unique passwords. A strong password – or passphrase – contains a complex (preferably irregular) combination of uppercase and lowercase letters, numbers, and other symbols; the more characters, the better. The How Secure Is My Password website can help. Alternatively, unique passwords vary from website to website. Using passwords that are both strong and unique is critical. Invariably, even the strongest passwords become weak when used everywhere, for everything.
3. Use a password manager on every device. Password management software facilitates the use of strong and unique passwords, for expert and novice users alike. Products like 1Password, Dashlane, and LastPass make creating unique and strong passwords a snap, and effortlessly sync your login credentials across Windows, Macintosh, and mobile devices.
4. Learn to spot phishing like your bank account depends upon it. Because it probably does. Phishing is the activity of defrauding an online account holder of financial or other confidential information by posing as a legitimate company. Phishing attempts now occur using email, social networking, telephone and other communications, but tell-tale signs often exist. Learn to spot these signs well, and approach unsolicited communication with caution. If it appears too good to be true, it probably is.
5. Make two-factor authentication a habit. If you’re really serious about security, then it’s probably time. Two-factor authentication, or 2FA as it’s commonly abbreviated, adds an extra step to your basic login procedure. Increasing in popularity and now built into a wide range of online systems, this extra step combines something you know with something you have to reliably verify your identity. Because passwords can be stolen, cracked, leaked, guessed, bought, phished, sniffed – or maybe even read from the sticky on your desk – 2FA will increase your safety immensely.